I got asked to look into a problem where two servers where not able to communicate with each other, ping didnt work and the application could not connect to the server. Firewall rules and routing was fine and my colleague spend already over an hour but couldnt find something. The first thing I asked, do you see a TCP connection? He told me yes over the ASDM logging I see something…. I double check and connect to the console and run:
show conn address 10.20.100.21
Show conn output:
TCP DMZ 10.10.127.29:2222 TRANSFER 10.20.100.21:42799, idle 0:00:00, bytes 0, flags saA TCP DMZ 10.10.127.29:2223 TRANSFER 10.20.100.21:63554, idle 0:00:00, bytes 0, flags saA TCP DMZ 10.5.63.29:2220 TRANSFER 10.20.100.21:59274, idle 0:00:00, bytes 0, flags saA TCP DMZ 10.5.63.29:2221 TRANSFER 10.20.100.21:55782, idle 0:00:00, bytes 0, flags saA
I saw directly that the TCP connection was not open because the connection flag was “saA” what means outbound SYN was send and a connection is reserved but no SYN ACK came back. The problem in the end was that between these two servers was a VPN and that the IP network was missing in both crypto map’s what was then easy to find and solve in the end.
The command “show conn ?” give you enough information and when it comes to troubleshooting that you need to know basic troubleshooting skills because some stuff is not easy to find out over the ASDM and to use the command line instead.
Here the overview over the ASA TCP connection flags which are important to know or at least to know where to look them up 😉
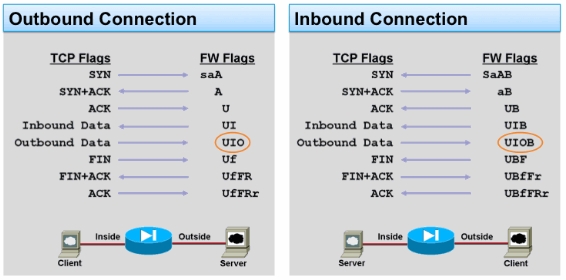
Here the document from Cisco: ASA TCP Connection Flags (Connection build-up and teardown)