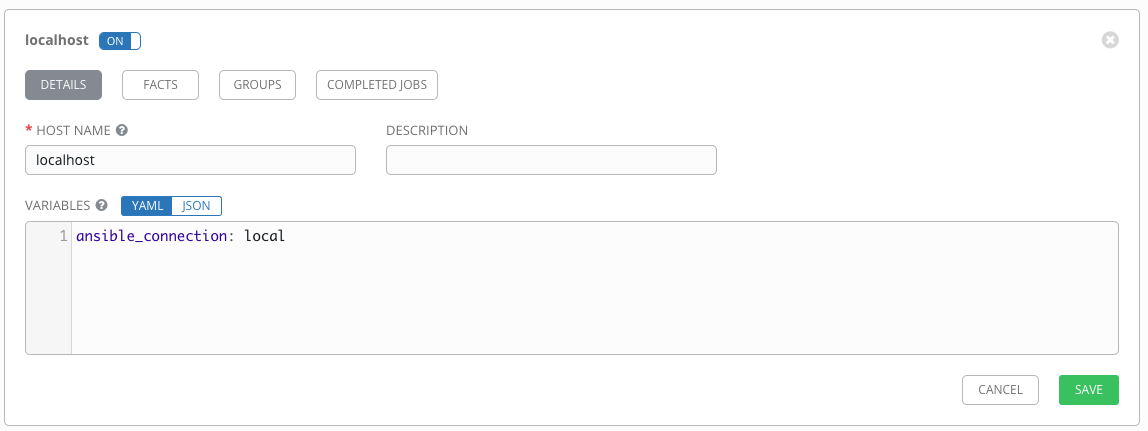
You might have seen my previous article about the OpenShift troubleshooting guide. With this blog post I want to show how to validate that an OpenShift container platform is fully functional. This is less of an issue when you do a fresh install but becomes more important when you apply changes or do in-place upgrades your cluster. And because we all like automation; I show how to do this with Ansible in an automated way.
Let’s jump right into it and look at the different steps. Here the links to the Ansible role and playbook for more details:
- Prepare workspace – create a temp directories and copy admin.kubeconfig there.
- Check node state – run command to check for Not Ready nodes:
-
oc get nodes --no-headers=true | grep -v ' Ready' | true
- Check node scheduling – run command to check for nodes where scheduling is disabled:
-
oc get nodes --no-headers=true | grep 'SchedulingDisabled' | awk '{ print $1 }' - Check master certificates – check validity of master API, controller and etcd certificates:
-
cat /etc/origin/master/ca.crt | openssl x509 -text | grep -i Validity -A2 cat /etc/origin/master/master.server.crt | openssl x509 -text | grep -i Validity -A2 cat /etc/origin/master/admin.crt | openssl x509 -text | grep -i Validity -A2 cat /etc/etcd/ca.crt | openssl x509 -text | grep -i Validity -A2
- Check nodes certificates – check validity of worker node certificate. This needs to run on all compute and infra nodes, not masters:
-
cat /etc/origin/node/server.crt | openssl x509 -text | grep -i Validity -A2
- Check etcd health – run command for cluster health check:
-
/usr/bin/etcdctl --cert-file /etc/etcd/peer.crt --key-file /etc/etcd/peer.key --ca-file /etc/etcd/ca.crt -C https://{{ hostname.stdout }}:2379 cluster-health - Check important default projects for failed pods – look out for failed pods:
-
oc get pods -o wide --no-headers=true -n {{ item }} | grep -v " Running\|Completed" || true - Check registry health – run GET docker-registry healthz path and expect http 200:
-
curl -kv https://{{ registry_ip.stdout }}/healthz - Check SkyDNS resolution – try to resolve internal hostnames:
-
nslookup docker-registry.default.svc.cluster.local nslookup docker-registry.default.svc
- Check upstream DNS resolution – try and resolve cluster external dns names.
- Create test project
- Run persistent volume test – create busybox container and claim volume
- apply imagestream, deploymentconfig and persistent volume claim configuration
- synchronise testfile to container pv
- check content of testfile
- delete testfile
- Run test build – run the following steps to create multiple application pods on the OpenShift cluster:
- apply buildconfig, imagestream, deploymentconfig, service and route configuration
- check pods are running
- get route hostnames
- connect to routes and show output
- trigger new-build and check new build is created
- check if pods are running
- connect to routes and show output
- Delete test project
- Delete workspace folder – at the end the validation the role deletes the temporary folder and all its contents.
Next we need to run the playbook and see the output below:
PLAY [Check OpenShift cluster installation] ***********************************************************************************************************************
TASK [check : make temp directory] ********************************************************************************************************************************
changed: [master1]
TASK [check : create temp directory] ******************************************************************************************************************************
ok: [master1]
TASK [check : create template folder] *****************************************************************************************************************************
changed: [master1]
TASK [check : create test file folder] ****************************************************************************************************************************
changed: [master1]
TASK [check : get hostname] ***************************************************************************************************************************************
changed: [master1]
TASK [check : copy admin config] **********************************************************************************************************************************
ok: [master1]
TASK [check : check for not ready nodes] **************************************************************************************************************************
changed: [master1]
TASK [check : not ready nodes] ************************************************************************************************************************************
ok: [master1] => {
"notready.stdout_lines": []
}
TASK [check : check for scheduling disabled nodes] ****************************************************************************************************************
changed: [master1]
TASK [check : scheduling disabled nodes] **************************************************************************************************************************
ok: [master1] => {
"schedulingdisabled.stdout_lines": []
}
TASK [check : validate master certificates] ***********************************************************************************************************************
changed: [master1] => (item=cat /etc/origin/master/ca.crt | openssl x509 -text | grep -i Validity -A2)
changed: [master1] => (item=cat /etc/origin/master/master.server.crt | openssl x509 -text | grep -i Validity -A2)
changed: [master1] => (item=cat /etc/origin/master/admin.crt | openssl x509 -text | grep -i Validity -A2)
changed: [master1] => (item=cat /etc/etcd/ca.crt | openssl x509 -text | grep -i Validity -A2)
TASK [check : ca certificate] *************************************************************************************************************************************
ok: [master1] => {
"msg": [
[
" Validity",
" Not Before: Jan 31 17:13:52 2019 GMT",
" Not After : Jan 30 17:13:53 2024 GMT"
],
[
" Validity",
" Not Before: Jan 31 17:13:53 2019 GMT",
" Not After : Jan 30 17:13:54 2021 GMT"
],
[
" Validity",
" Not Before: Jan 31 17:13:53 2019 GMT",
" Not After : Jan 30 17:13:54 2021 GMT"
],
[
" Validity",
" Not Before: Jan 31 17:11:09 2019 GMT",
" Not After : Jan 30 17:11:09 2024 GMT"
]
]
}
TASK [check : check etcd state] ***********************************************************************************************************************************
changed: [master1]
TASK [check : show etcd state] ************************************************************************************************************************************
ok: [master1] => {
"etcdstate.stdout_lines": [
"member 335450512aab5650 is healthy: got healthy result from https://172.26.7.132:2379",
"cluster is healthy"
]
}
TASK [check : check default openshift-infra and logging projects for failed pods] *********************************************************************************
ok: [master1] => (item=default)
ok: [master1] => (item=kube-system)
ok: [master1] => (item=kube-service-catalog)
ok: [master1] => (item=openshift-logging)
ok: [master1] => (item=openshift-infra)
ok: [master1] => (item=openshift-console)
ok: [master1] => (item=openshift-web-console)
ok: [master1] => (item=openshift-monitoring)
ok: [master1] => (item=openshift-node)
ok: [master1] => (item=openshift-sdn)
TASK [check : failed failedpods] **********************************************************************************************************************************
ok: [master1] => {
"msg": [
[],
[],
[],
[],
[],
[],
[],
[],
[],
[]
]
}
TASK [check : get container registry ip] **************************************************************************************************************************
changed: [master1]
TASK [check : check container registry health] ********************************************************************************************************************
ok: [master1]
TASK [check : check internal SysDNS resolution for cluster.local] *************************************************************************************************
changed: [master1] => (item=docker-registry.default.svc.cluster.local)
changed: [master1] => (item=docker-registry.default.svc)
TASK [check : check external DNS upstream resolution] *************************************************************************************************************
changed: [master1] => (item=www.google.com)
changed: [master1] => (item=www.google.co.uk)
changed: [master1] => (item=www.google.de)
TASK [check : create test project] ********************************************************************************************************************************
changed: [master1]
TASK [check : run test persistent volume] *************************************************************************************************************************
included: /var/jenkins_home/workspace/openshift/ansible/roles/check/tasks/pv.yml for master1
TASK [check : create sequence number list for pv] *****************************************************************************************************************
ok: [master1] => (item=1)
ok: [master1] => (item=2)
ok: [master1] => (item=3)
ok: [master1] => (item=4)
ok: [master1] => (item=5)
TASK [check : copy build templates] *******************************************************************************************************************************
changed: [master1] => (item={u'dest': u'busybox.yml', u'src': u'busybox.j2'})
changed: [master1] => (item={u'dest': u'pv.yml', u'src': u'pv.j2'})
TASK [check : copy testfile] **************************************************************************************************************************************
changed: [master1]
TASK [check : create pvs] *****************************************************************************************************************************************
ok: [master1]
TASK [check : deploy busybox pod] *********************************************************************************************************************************
changed: [master1]
TASK [check : check if all pods are running] **********************************************************************************************************************
FAILED - RETRYING: check if all pods are running (10 retries left).
changed: [master1] => (item=busybox)
TASK [check : get busybox pod name] *******************************************************************************************************************************
changed: [master1]
TASK [check : sync testfile to pod] *******************************************************************************************************************************
changed: [master1]
TASK [check : check testfile in pv] *******************************************************************************************************************************
changed: [master1]
TASK [check : delete testfile in pv] ******************************************************************************************************************************
changed: [master1]
TASK [check : run test build] *************************************************************************************************************************************
included: /var/jenkins_home/workspace/openshift/ansible/roles/check/tasks/build.yml for master1
TASK [check : create sequence number list for hello openshift] ****************************************************************************************************
ok: [master1] => (item=0)
ok: [master1] => (item=1)
ok: [master1] => (item=2)
ok: [master1] => (item=3)
ok: [master1] => (item=4)
ok: [master1] => (item=5)
ok: [master1] => (item=6)
ok: [master1] => (item=7)
ok: [master1] => (item=8)
ok: [master1] => (item=9)
TASK [check : create pod list] ************************************************************************************************************************************
ok: [master1] => (item=[u'0', {u'svc': u'http'}])
ok: [master1] => (item=[u'1', {u'svc': u'http'}])
ok: [master1] => (item=[u'2', {u'svc': u'http'}])
ok: [master1] => (item=[u'3', {u'svc': u'http'}])
ok: [master1] => (item=[u'4', {u'svc': u'http'}])
ok: [master1] => (item=[u'5', {u'svc': u'http'}])
ok: [master1] => (item=[u'6', {u'svc': u'http'}])
ok: [master1] => (item=[u'7', {u'svc': u'http'}])
ok: [master1] => (item=[u'8', {u'svc': u'http'}])
ok: [master1] => (item=[u'9', {u'svc': u'http'}])
TASK [check : copy build templates] *******************************************************************************************************************************
changed: [master1] => (item={u'dest': u'hello-openshift.yml', u'src': u'hello-openshift.j2'})
TASK [check : deploy hello openshift pods] ************************************************************************************************************************
changed: [master1]
TASK [check : check if all pods are running] **********************************************************************************************************************
FAILED - RETRYING: check if all pods are running (10 retries left).
changed: [master1] => (item={u'name': u'hello-http-0'})
FAILED - RETRYING: check if all pods are running (10 retries left).
changed: [master1] => (item={u'name': u'hello-http-1'})
changed: [master1] => (item={u'name': u'hello-http-2'})
changed: [master1] => (item={u'name': u'hello-http-3'})
changed: [master1] => (item={u'name': u'hello-http-4'})
changed: [master1] => (item={u'name': u'hello-http-5'})
changed: [master1] => (item={u'name': u'hello-http-6'})
changed: [master1] => (item={u'name': u'hello-http-7'})
changed: [master1] => (item={u'name': u'hello-http-8'})
changed: [master1] => (item={u'name': u'hello-http-9'})
TASK [check : get hello openshift pod hostnames] ******************************************************************************************************************
changed: [master1]
TASK [check : convert check_route string to json] *****************************************************************************************************************
ok: [master1]
TASK [check : set query to get pod hostname] **********************************************************************************************************************
ok: [master1]
TASK [check : get hostname list] **********************************************************************************************************************************
ok: [master1]
TASK [check : connect to route via curl] **************************************************************************************************************************
changed: [master1] => (item=hello-http-0-test.paas.domain.com)
changed: [master1] => (item=hello-http-1-test.paas.domain.com)
changed: [master1] => (item=hello-http-2-test.paas.domain.com)
changed: [master1] => (item=hello-http-3-test.paas.domain.com)
changed: [master1] => (item=hello-http-4-test.paas.domain.com)
changed: [master1] => (item=hello-http-5-test.paas.domain.com)
changed: [master1] => (item=hello-http-6-test.paas.domain.com)
changed: [master1] => (item=hello-http-7-test.paas.domain.com)
changed: [master1] => (item=hello-http-8-test.paas.domain.com)
changed: [master1] => (item=hello-http-9-test.paas.domain.com)
TASK [check : set json query] *************************************************************************************************************************************
ok: [master1]
TASK [check : show route http response] ***************************************************************************************************************************
ok: [master1] => {
"msg": [
"hello-http-0",
"hello-http-1",
"hello-http-2",
"hello-http-3",
"hello-http-4",
"hello-http-5",
"hello-http-6",
"hello-http-7",
"hello-http-8",
"hello-http-9"
]
}
TASK [check : trigger new build] **********************************************************************************************************************************
changed: [master1]
TASK [check : check new build is created] *************************************************************************************************************************
changed: [master1]
TASK [check : check if all pods with new build are running] *******************************************************************************************************
FAILED - RETRYING: check if all pods with new build are running (10 retries left).
FAILED - RETRYING: check if all pods with new build are running (9 retries left).
changed: [master1] => (item={u'name': u'hello-http-0'})
changed: [master1] => (item={u'name': u'hello-http-1'})
changed: [master1] => (item={u'name': u'hello-http-2'})
changed: [master1] => (item={u'name': u'hello-http-3'})
changed: [master1] => (item={u'name': u'hello-http-4'})
changed: [master1] => (item={u'name': u'hello-http-5'})
changed: [master1] => (item={u'name': u'hello-http-6'})
changed: [master1] => (item={u'name': u'hello-http-7'})
changed: [master1] => (item={u'name': u'hello-http-8'})
changed: [master1] => (item={u'name': u'hello-http-9'})
TASK [check : connect to route via curl] **************************************************************************************************************************
changed: [master1] => (item=hello-http-0-test.paas.domain.com)
changed: [master1] => (item=hello-http-1-test.paas.domain.com)
changed: [master1] => (item=hello-http-2-test.paas.domain.com)
changed: [master1] => (item=hello-http-3-test.paas.domain.com)
changed: [master1] => (item=hello-http-4-test.paas.domain.com)
changed: [master1] => (item=hello-http-5-test.paas.domain.com)
changed: [master1] => (item=hello-http-6-test.paas.domain.com)
changed: [master1] => (item=hello-http-7-test.paas.domain.com)
changed: [master1] => (item=hello-http-8-test.paas.domain.com)
changed: [master1] => (item=hello-http-9-test.paas.domain.com)
TASK [check : show route http response] ***************************************************************************************************************************
ok: [master1] => {
"msg": [
"hello-http-0",
"hello-http-1",
"hello-http-2",
"hello-http-3",
"hello-http-4",
"hello-http-5",
"hello-http-6",
"hello-http-7",
"hello-http-8",
"hello-http-9"
]
}
TASK [check : delete test project] ********************************************************************************************************************************
changed: [master1]
TASK [check : delete temp directory] ******************************************************************************************************************************
ok: [master1]
PLAY RECAP ********************************************************************************************************************************************************
master1 : ok=52 changed=30 unreachable=0 failed=0
The cluster validation playbook successfully finished without errors and this is just a simple way to do a basic check of your OpenShift platform. Check out the OpenShift documentation about environment_health_checks.