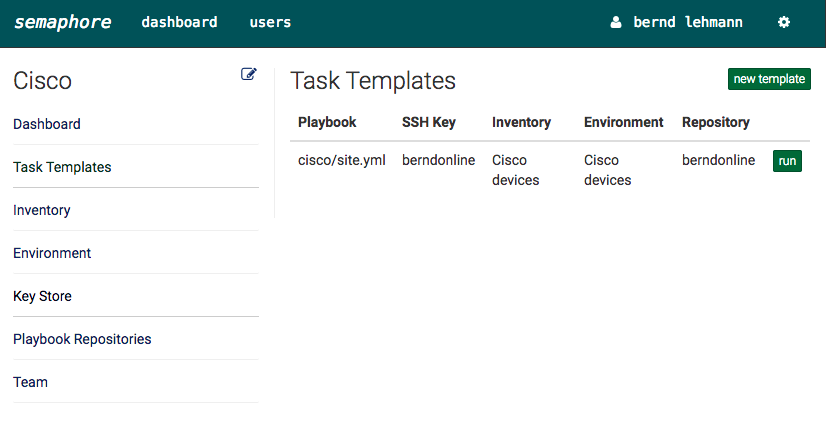
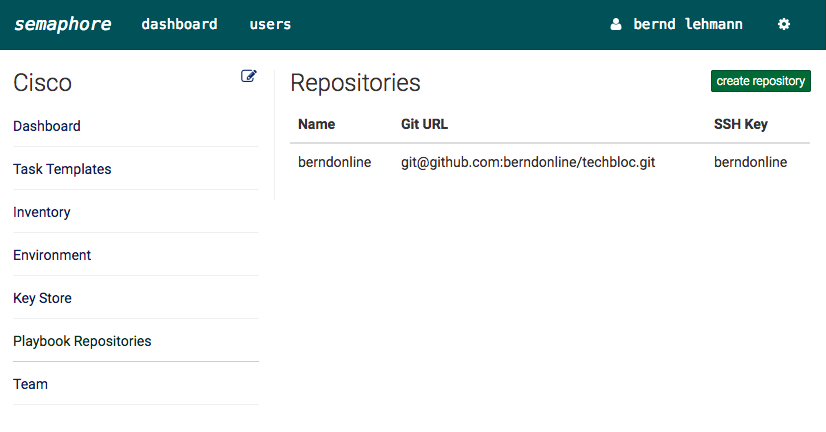
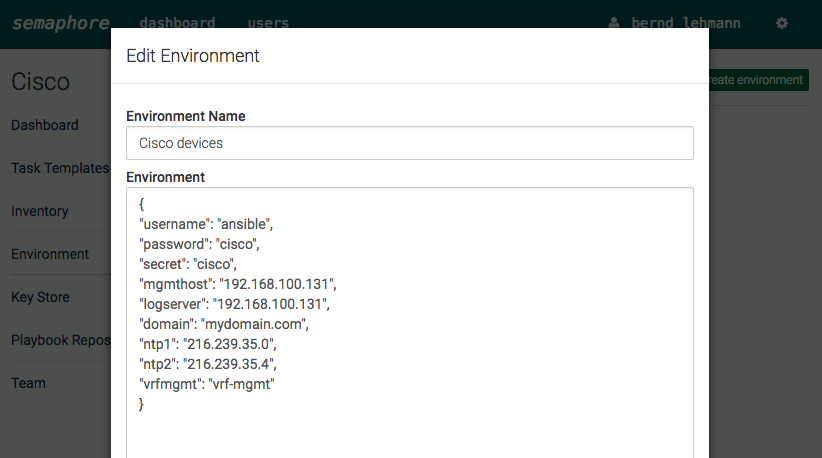
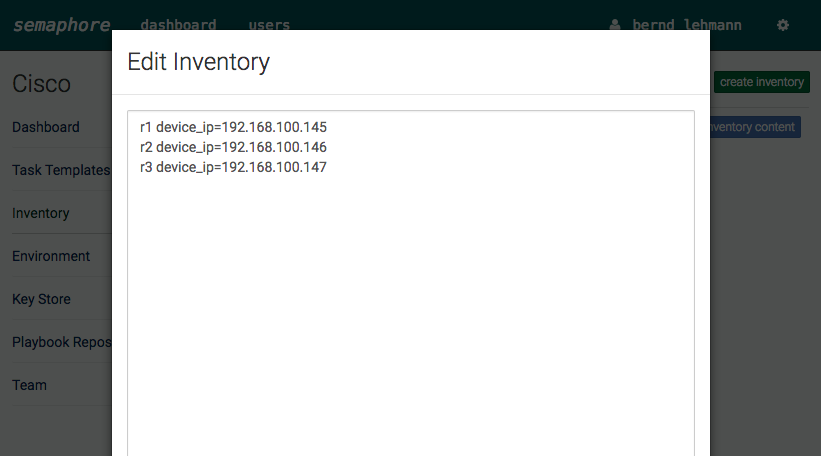
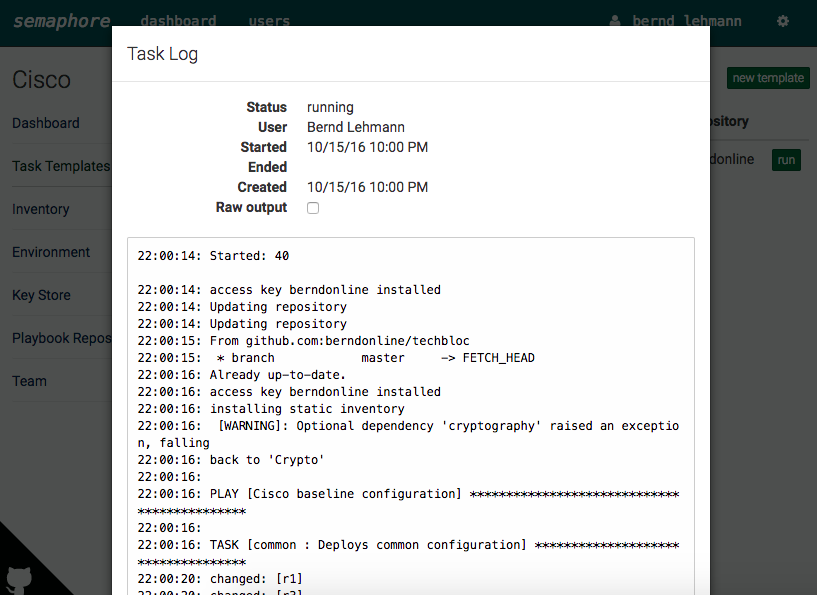
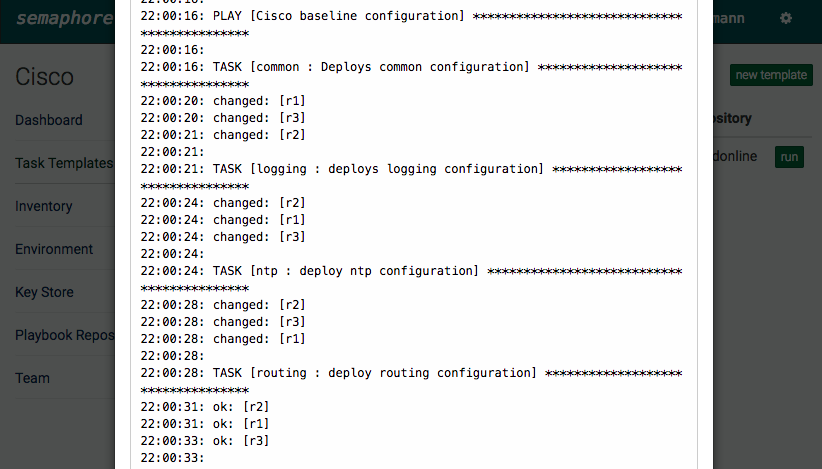
Like in my previous post in the new development version 2.2. from Ansible are new IOS and ASA core modules.
Here an example of the asa_config and asa_acl module to create and object-group in the first step and create the inside create access-list:
- name: Cisco ASA access-list config
connection: local
hosts: firewall
gather_facts: false
vars:
cli:
username: "{{ username }}"
password: "{{ password }}"
host: "{{ device_ip }}"
authorize: yes
auth_pass: cisco
tasks:
- name: create object group
asa_config:
lines:
- network-object host 10.1.0.1
- network-object host 10.1.0.2
- network-object host 10.1.0.3
parents: ['object-group network dummy-group']
provider: "{{ cli }}"
# register: result
- name: configure access-list
asa_acl:
lines:
- access-list acl_inside extended permit tcp object-group dummy-group any eq www
- access-list acl_inside extended permit udp object-group dummy-group any eq domain
- access-list acl_inside extended deny ip any any
before: clear configure access-list acl_inside
match: strict
replace: block
provider: "{{ cli }}"
# register: result
- debug: var=result
Here output when you run the playbook the first time:
ansible-playbook cisco/asa_access-list_config.yml -i cisco/hosts
PLAY [Cisco ASA access-list config] ********************************************
TASK [create object group] *****************************************************
changed: [fw1]
TASK [configure access-list] ***************************************************
changed: [fw1]
TASK [debug] *******************************************************************
ok: [fw1] => {
"result": "VARIABLE IS NOT DEFINED!"
}
PLAY RECAP *********************************************************************
fw1 : ok=3 changed=2 unreachable=0 failed=0
Here the output then you run the playbook a second time, you see nothing is changed:
ansible-playbook cisco/asa_access-list_config.yml -i cisco/hosts
PLAY [Cisco ASA access-list config] ********************************************
TASK [create object group] *****************************************************
ok: [fw1]
TASK [configure access-list] ***************************************************
ok: [fw1]
TASK [debug] *******************************************************************
ok: [fw1] => {
"result": "VARIABLE IS NOT DEFINED!"
}
PLAY RECAP *********************************************************************
fw1 : ok=3 changed=0 unreachable=0 failed=0
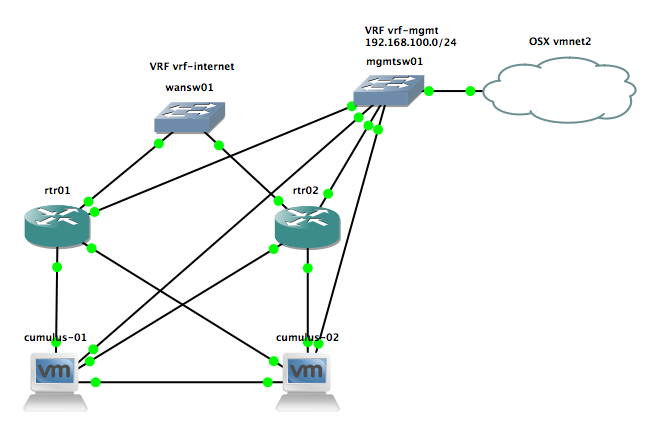
Read my new post about an Ansible Playbook for Cisco ASAv Firewall Topology