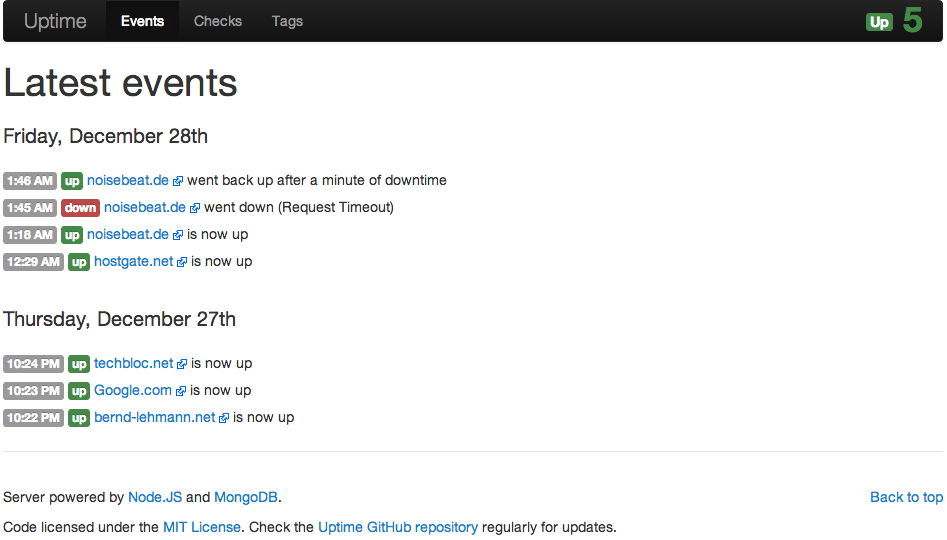
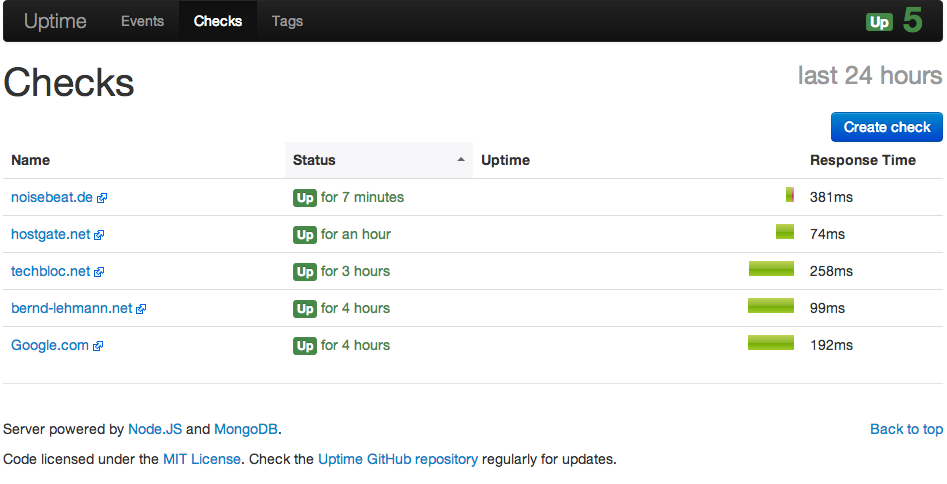
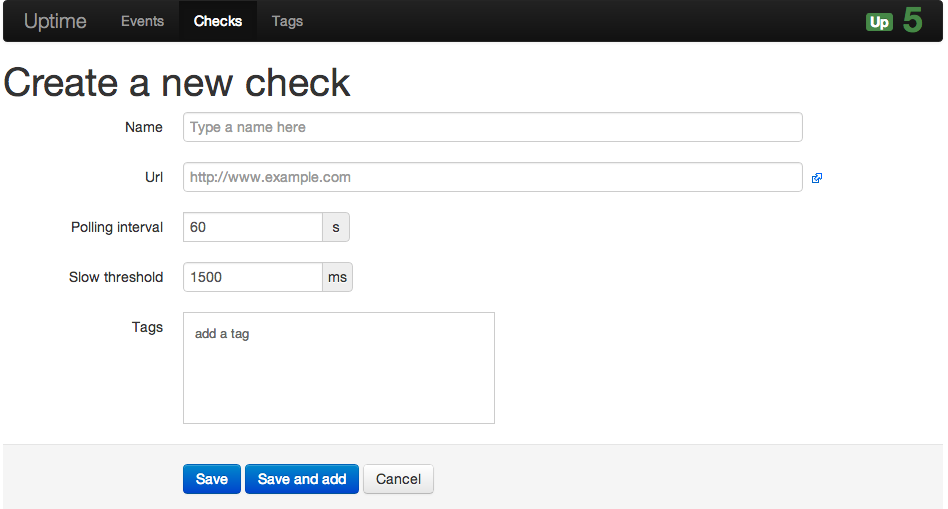
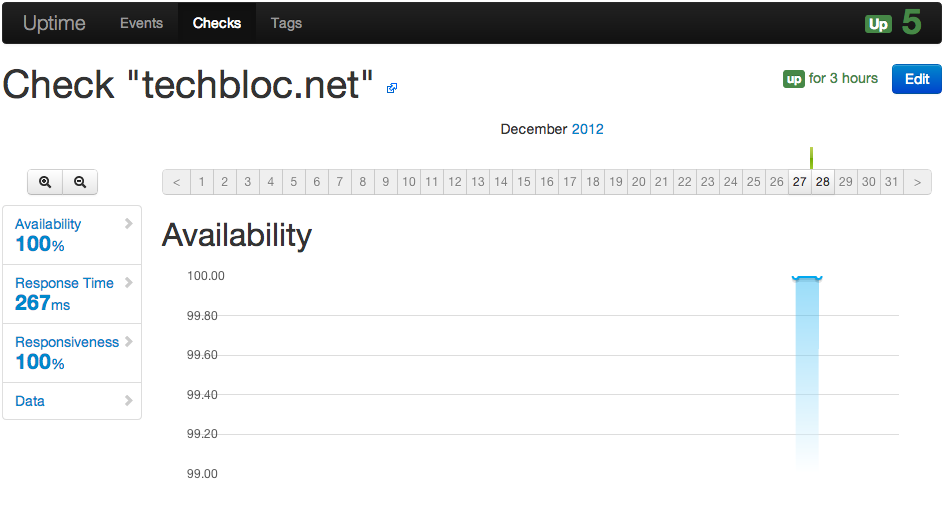
At the moment I play around with Cisco SSL VPN (WebVPN) and here some steps how to configured these on an Cisco ASA. SSL VPN is on one hand the Cisco Anyconnect client and on the other an Clientless SSL VPN over a portal what is running on the ASA.
I will not go into much detail here, it’s more basic configurations steps you need to configure to get it running.
For a basic set-up we need two network objects
object network inside-subnet
subnet 172.16.0.0 255.240.0.0
exit
object network sslvpn-subnet
subnet 172.31.250.0 255.255.255.0
exit
Then we define the DHCP pool for Anyconnect connections
ip local pool SSLVPNClientPool 172.31.250.1-172.31.250.250 mask 255.255.255.0
We also need to make sure that Anyconnect clients communication with their original IP address and for that we need the following nat statement
nat (inside,outside) source static inside-subnet inside-subnet destination static sslvpn-subnet sslvpn-subnet
Here you select the Anyconnect package what you need to upload to your flash before and enable webvpn on your outside interface
webvpn
anyconnect image disk0:/anyconnect-win-2.4.1012-k9.pkg 1
enable outside
anyconnect enable
exit
In the SSL VPN client policy we define name server, domain name and DHCP pool. We also define here Anyconnect with ssl-client and the portal with ssl-clientless
group-policy SSLVPNClientPolicy internal
group-policy SSLVPNClientPolicy attributes
dns-server value 172.16.0.12
default-domain value domain.com
address-pools value SSLVPNClientPool
vpn-tunnel-protocol ssl-client ssl-clientless
exit
We configure an SSL VPN tunnel group for remote access and set default policy to the SSL VPN client policy we configured in the step before
tunnel-group SSLVPNClientProfile type remote-access
tunnel-group SSLVPNClientProfile general-attributes
default-group-policy SSLVPNClientPolicy
exit
Next, we define an external aaa server in my example an Windows Active Directory
aaa-server ldap-group protocol ldap
aaa-server ldap-group (inside) host 172.16.0.12
ldap-base-dn OU=Departments, OU=DE, OU=Company, DC=domain,DC=com
ldap-login-dn cn=LDAPReader, OU=ServiceAccounts, OU=Company, DC=domain, DC=com
ldap-login-password secretpassword
ldap-naming-attribute sAMAccountName
ldap-scope subtree
server-type microsoft
exit
After we configured the external aaa server we need to link that in the tunnel group
tunnel-group SSLVPNClientProfile webvpn-attributes
group-alias SSLVPNClient enable
authentication-server-group ldap-group
exit
One of the last steps we enable the tunnel group within webvpn and configure sysopt permit-vpn
webvpn
tunnel-group-list enable
exit
sysopt connection permit-vpn
With the following command you can enable NTLM for a whole subnet if you use Windows IIS and integrate authentication
auto-signon allow ip 172.16.0.0 255.255.255.0 auth-type ntlm
That’s it, quite easy and clear setup over the command line, you can also click yourself through the ASDM but it will definitively take longer.